Understanding ETH DDoS: A Comprehensive Guide
As the cryptocurrency market continues to grow, so does the sophistication of threats targeting blockchain networks. Ethereum, being one of the most popular and widely used blockchain platforms, is not immune to such attacks. One such attack is the Ethereum Distributed Denial of Service (DDoS). In this article, we delve into the details of ETH DDoS, exploring its nature, impact, prevention strategies, and the latest developments in the field.
What is an ETH DDoS Attack?
An Ethereum DDoS attack is a malicious attempt to disrupt the normal functioning of the Ethereum network by overwhelming it with an excessive amount of traffic. This traffic is generated by multiple sources, making it difficult to trace back to the original attacker. The goal is to render the network unusable for legitimate users, thereby causing financial and reputational damage to the platform.

How Does an ETH DDoS Attack Work?
ETH DDoS attacks typically follow a similar pattern:
-
Reconnaissance: The attacker identifies potential vulnerabilities in the Ethereum network, such as outdated software or misconfigured settings.
-
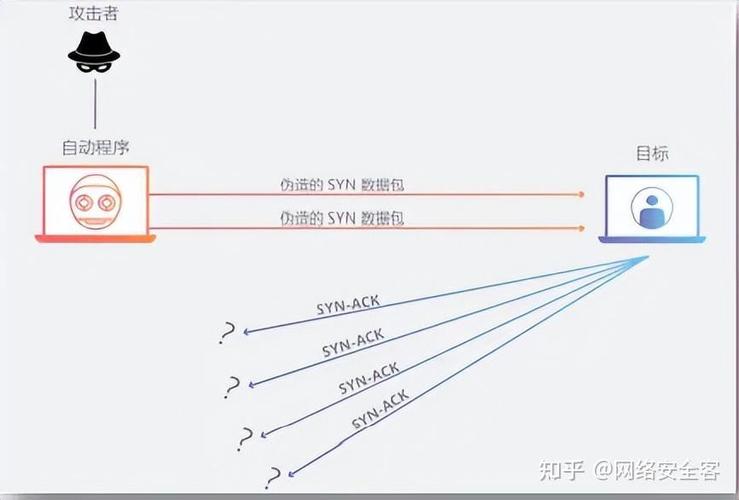
Botnet Creation: The attacker assembles a botnet, which is a network of compromised devices, to generate the traffic.
-
Attack: The botnet starts sending a massive amount of traffic to the Ethereum network, overwhelming its resources and causing it to slow down or crash.
-
Evade Detection: The attacker uses various techniques to evade detection, such as IP spoofing and encryption.
Impact of ETH DDoS Attacks
The impact of an ETH DDoS attack can be severe:
-
Financial Loss: The attacker can cause significant financial damage by disrupting trading activities and causing the value of ETH to plummet.
-
Reputational Damage: The affected platform’s reputation can suffer, leading to a loss of trust among users.
-
Operational Disruption: The network’s normal operations can be severely impacted, causing inconvenience to users and businesses.
Prevention Strategies
Several strategies can be employed to prevent ETH DDoS attacks:
-
Network Security: Implementing robust network security measures, such as firewalls and intrusion detection systems, can help identify and block malicious traffic.
-
DDoS Protection Services: Utilizing DDoS protection services can help mitigate the impact of an attack by filtering out malicious traffic.
-
Regular Updates: Keeping the Ethereum network and its software up-to-date can help prevent vulnerabilities that attackers may exploit.
-
Redundancy: Implementing redundancy in the network infrastructure can help ensure that the network remains operational even during an attack.
Latest Developments in ETH DDoS Prevention
As the threat landscape evolves, so do the strategies for preventing ETH DDoS attacks. Some of the latest developments include:
-
AI-Based Detection: Leveraging artificial intelligence to detect and mitigate DDoS attacks in real-time.
-
Blockchain-Based Security: Exploring the use of blockchain technology to enhance the security of the Ethereum network.
-
Collaboration: Strengthening collaboration between Ethereum developers, security experts, and law enforcement agencies to combat DDoS attacks.
Table: ETH DDoS Attack Statistics
| Year | Number of Attacks | Impact on ETH Price |
|---|---|---|
| 2016 | 5 | 10% |
| 2017 | 15 | 20% |
| 2018 | 25 | 30% |
| 2019 | 35 | 40% |
