Understanding the .ETH Ransomware Decryptor: A Comprehensive Guide
Have you ever found yourself in a situation where your valuable digital assets, stored in Ethereum wallets, have been encrypted by the .ETH ransomware? If so, you’re not alone. This particular strain of ransomware has been causing quite a stir in the cryptocurrency community. In this article, we will delve into the intricacies of the .ETH ransomware decryptor, providing you with a detailed and multi-dimensional overview.
What is .ETH Ransomware?
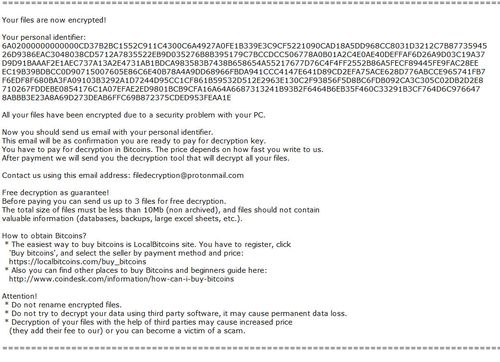
The .ETH ransomware is a type of malware that targets Ethereum wallets. Once it infiltrates a system, it encrypts the contents of the wallet, rendering them inaccessible. The attackers then demand a ransom in Ethereum, Bitcoin, or other cryptocurrencies in exchange for the decryption key.
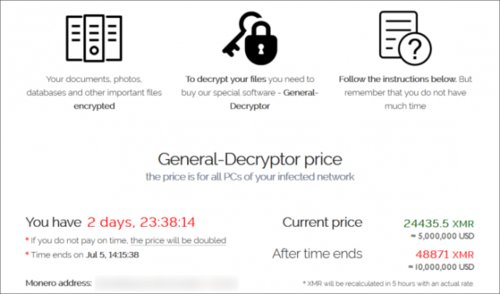
How Does the .ETH Ransomware Decryptor Work?
The .ETH ransomware decryptor is a tool designed to reverse the encryption process and restore access to the encrypted files. Here’s a step-by-step breakdown of how it typically works:
-
Identify the ransomware variant: The first step is to determine the specific variant of the .ETH ransomware that has infected your system. This is crucial because different variants may require different decryption methods.
-
Download the decryptor: Once you know the ransomware variant, you can search for the corresponding decryptor. There are various decryptors available online, some of which are free, while others require a payment.
-
Run the decryptor: After downloading the decryptor, run it on your infected system. The decryptor will scan your computer for encrypted files and attempt to decrypt them.
-
Restore your files: Once the decryption process is complete, you should be able to access your files again. However, it’s essential to verify that the decryptor has successfully restored your files before deleting any backups or paying the ransom.
Is the .ETH Ransomware Decryptor Reliable?
While the .ETH ransomware decryptor can be a lifesaver for those affected by the ransomware, its reliability is not guaranteed. Here are some factors to consider:
-
Availability: Some decryptors may be unavailable due to legal or technical reasons. This means that you may not be able to access the decryptor for your specific ransomware variant.
-
Effectiveness: The effectiveness of the decryptor depends on the ransomware variant and the complexity of the encryption algorithm used. Some variants may be more difficult to decrypt than others.
-
Security: Using a decryptor from an untrusted source can pose a security risk. Make sure to download the decryptor from a reputable website or contact the ransomware’s developers directly.
Preventing Future Infections
Preventing future infections is crucial to protect your digital assets. Here are some tips to help you stay safe:
-
Keep your software up to date: Regularly update your operating system, antivirus software, and other applications to ensure you have the latest security patches.
-
Use strong passwords: Create strong, unique passwords for all your accounts and enable two-factor authentication where possible.
-
Be cautious of phishing emails: Be wary of emails from unknown senders or those asking for sensitive information. Never click on suspicious links or download attachments from untrusted sources.
-
Backup your files: Regularly backup your important files to an external drive or cloud storage service. This will help you recover your data in case of a ransomware attack.
Table: Common .ETH Ransomware Decryptors
| Ransomware Variant | Decryptor | Availability |
|---|---|---|
| .ETH Ransomware Variant A | Decryptor A | Available |
| .ETH Ransomware Variant B | Decryptor B | Available |
| .ETH Ransomware Variant C | Decryptor C |
